DAMM - Differential Analysis of Malware in Memory
An open source memory analysis tool built on top of Volatility. It is
meant as a proving ground for interesting new techniques to be made
available to the community. These techniques are an attempt to speed up
the investigation process through data reduction and codifying some
expert knowledge.
Features
- ~30 Volatility plugins combined into ~20 DAMM plugins (e.g., pslist, psxview and other elements are combined into a 'processes' plugin)
- Can run multiple plugins in one invocation
- The option to store plugin results in SQLite databases for preservation or for "cached" analysis
- A filtering/type system that allows easily filtering on attributes like pids to see all information related to some process and exact or partial matching for strings, etc.
- The ability to show the differences between two databases of results for the same or similar machines and manipulate from the cmdline how the differencing operates
- The ability to warn on certain types of suspicious behavior
- Output for terminal, tsv or grepable
NOTE: Most DAMM output looks better piped through 'less -S' (upper 'S') as in:
#python damm.py <some DAMM functionality> | less -S (for default output format)
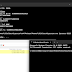
python damm.py -h
usage: damm.py [-h] [-d DIR] [-p PLUGIN [PLUGIN ...]] [-f FILE] [-k KDBG]
[--db DB] [--profile PROFILE] [--debug] [--info] [--tsv]
[--grepable] [--filter FILTER] [--filtertype FILTERTYPE]
[--diff BASELINE] [-u FIELD [FIELD ...]] [--warnings] [-q]
DAMM v1.0 Beta
optional arguments:
-h, --help show this help message and exit
-d DIR Path to additional plugin directory
-p PLUGIN [PLUGIN ...]
Plugin(s) to run. For a list of options use --info
-f FILE Memory image file to run plugin on
-k KDBG KDBG address for the images (in hex)
--db DB SQLite db file, for efficient input/output
--profile PROFILE Volatility profile for the images (e.g. WinXPSP2x86)
--debug Print debugging statements
--info Print available volatility profiles, plugins
--tsv Print screen formatted output.
--grepable Print in grepable text format
--filter FILTER Filter results on name:value pair, e.g., pid:42
--filtertype FILTERTYPE
Filter match type; either "exact" or "partial",
defaults to partial
--diff BASELINE Diff the imageFile|db with this db file as a baseline
-u FIELD [FIELD ...] Use the specified fields to determine uniqueness of
memobjs when diffing
--warnings Look for suspicious objects.
-q Query the supplied db (via --db).
Supported plugins
See #python damm.py --info
apihooks callbacks connections devicetree dlls evtlogs handles idt
injections messagehooks mftentries modules mutants privileges processes
services sids timers
DAMM - Differential Analysis of Malware in Memory
![DAMM - Differential Analysis of Malware in Memory]() Reviewed by Zion3R
on
6:47 PM
Rating:
Reviewed by Zion3R
on
6:47 PM
Rating: