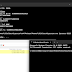
FastIR Collector - Windows Incident Response Tool
This tool collects different artefacts on live Windows and records the results in csv files. With the analyses of this artefacts, an early compromission can be detected.
Requirements
- pywin32
- python WMI
- python psutil
- python yaml
- construct
- distorm3
- hexdump
- pytz
Execution
- ./fastIR_x64.py -h for help
- ./fastIR_x64.py --packages all extract all artefacts without dump package artefacts
- ./fastIR_x64.py --packages dump --dump mft to extract MFT
- ./fastIR_x64.py --packages all --ouput_dir your_ouput_dir to set the directory output (by default is the current directory)
- ./fastIR_x64.py --profile you_file_profile to set your own profile extraction
Packages
Packages Lists and Artefact
- fs
- IE History
- Named Pipes
- Prefetch
- Recycle-bin
- health
- ARP Table
- Drives list
- Network drives
- Networks Cards
- Processes
- Routes Tables
- Tasks
- Scheluded jobs
- Services
- Sessions
- Network Shares
- Sockets
- registry
- Installer Folders
- OpenSaveMRU
- Recents Docs
- Services
- Shellbags
- Autoruns
- USB History
- Userassists
- memory
- Clipboard
- dlls loaded
- Opened Files
- dump
- MFT we use AnalyseMFT for https://github.com/dkovar/analyzeMFT
- MBR
- RAM
- DISK
- FileCatcher
- based on mime type
- possibility to filter your search
- Yara Rules
A post about FastIR Collector and advanced Threats can be consulted here: http://www.sekoia.fr/blog/fastir-collector-on-advanced-threats
with the paper: http://www.sekoia.fr/blog/wp-content/uploads/2015/10/FastIR-Collector-on-advanced-threats_v1.4.pdf
FastIR Collector - Windows Incident Response Tool
 Reviewed by Zion3R
on
5:30 PM
Rating:
Reviewed by Zion3R
on
5:30 PM
Rating:
 Reviewed by Zion3R
on
5:30 PM
Rating:
Reviewed by Zion3R
on
5:30 PM
Rating: